Power management reference
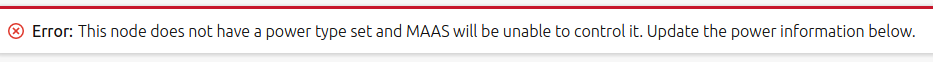
To manage a machine, MAAS must be able to power cycle it, usually through the machine’s BMC↗ card. Until you configure the power type, a newly-added machine can’t be enlisted and used by MAAS.
We require the user to explicitly set the cipher suite due to the fact that one BMC’s order is different from another, leading to erroneous discovery. You can explicitly select which cipher suite to use when interacting with a BMC. You do this by selecting the cipher suite in power configuration. By default, the cipher suite is 3. This is the least secure suite. It is up to you to select a more secure suite if supported and desired.
Power management reference guide
This article will help you learn:
- How to configure a machine’s power type
- How to configure and use IBM Z with MAAS
- How to use the virsh power type
- Which BMC drivers are supported
In addition, this article provides a complete catalogue of power parameters, by type.
You may also like to try maaspower↗ which is a community project designed to be used with the MAAS webhook driver. It is a pluggable system that accepts MAAS webhooks and can translate them to other external systems. Note: it is not supported by Canonical.
How to configure a machine’s power type
To configure a machine’s power type, click on the machine from the ‘Machines’ page of the web UI, then select its ‘Configuration’ tab. Scroll down until you find the Power configuration. If the power type is undefined, the following will be displayed:
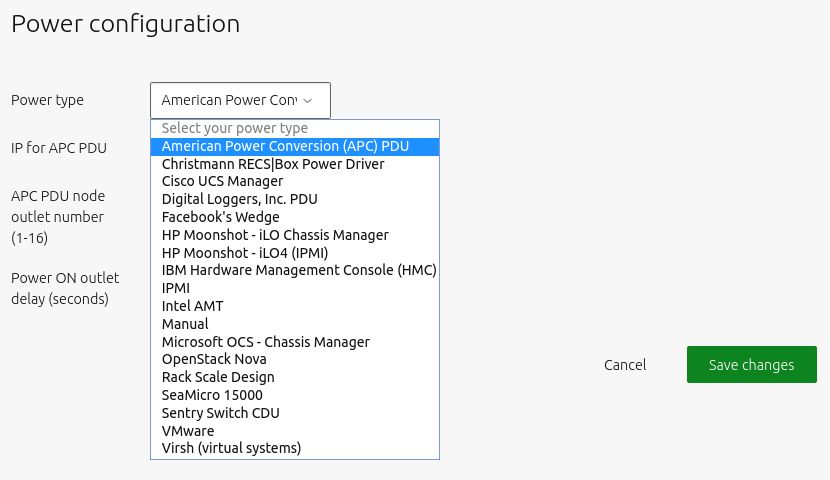
Choose a type in the drop-down menu that corresponds to the machine’s underlying machine’s BMC card.
Fill in the resulting form; the information required will depends on the power type:
| CLI power_type code | Description |
|---|---|
| amt | Intel AMT |
| apc | American Power Conversion (APC) PDU |
| dli | Digital Loggers, Inc. PDU |
| hmc | IBM Hardware Management Console (HMC) |
| lxd | LXD VM |
| ipmi | IPMI |
| manual | Manual power configuration |
| moonshot | HP Moonshot - iLO4 (IPMI) |
| mscm | HP Moonshot - iLO Chassis Manager |
| msftocs | Microsoft OCS - Chassis Manager |
| nova | OpenStack Nova |
| openbmc | OpenBMC Power Driver |
| proxmox | ProxMox Power Driver |
| recs_box | Christmann RECS-Box Power Driver |
| redfish | Redfish |
| sm15k | SeaMicro 15000 |
| ucsm | Cisco UCS Manager |
| virsh | libvirt KVM |
| vmware | VMware |
| webhook | Webhook |
| wedge | Facebook’s Wedge |
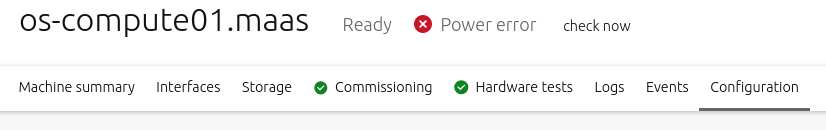
Click ‘Save changes’ to finish. Once that’s done, MAAS performs a power check on the machine. A successful power check is a good indication that MAAS can properly communicate with the machine, that is, it should quickly result in a power status of “Power off”. A failed attempt will show:
If you see this error, double-check your entered values by editing the power type, or consider another power type altogether.
Another possible cause for this error may be the networking: traffic may be getting filtered between the rack controller and the BMC card.
The following catalogue helps to explain the fields in the “create machine” dialogue above. Note that most of the multiple-choice fields have drop-down menus to assist with your choice.
| Form field | Description | Required |
|---|---|---|
| Power password | Password to access unit | Optional |
| Power address | IP address of unit | Required |
American Power Conversion (APC) PDU
| Form field | Description | Required |
|---|---|---|
| IP for APC PDU | IP address of unit | Required |
| APU PDU node outlet number (1-16) | PDU node outlet number | Required |
| Power ON outlet delay (seconds) | outlet power ON delay | Optional, default=5 |
| Form field | Description | Required |
|---|---|---|
| Outlet ID | outlet ID | Required |
| Power address | IP address of unit | Required |
| Power user | Username to login | Optional |
| Power password | Password to access unit | Optional |
IBM Hardware Management Console (HMC)
| Form field | Description | Required |
|---|---|---|
| IP for HMC | IP address of unit | Required |
| HMC username | Username to login | Optional |
| HMC password | Password to access unit | Optional |
| HMC Managed System server name | HMC managed server name | Required |
| HMC logical partition | HMC logical partition of unit | Required |
| Form field | Description | Required |
|---|---|---|
| LXD address | IP address of unit | Required |
| Instance name | LXD container instance name | Required |
| LXD password | Password to access unit | Optional |
Some of the fields for this power type have fixed choices, indicated in the “Choices” column.
| Form field | Description | Choices | Required |
|---|---|---|---|
| Power driver | Power driver | LAN [IPMI 1.5] |
Required |
LAN_2_0 [IPMI 2.0] |
|||
| Power boot type | Boot type | Automatic |
Required |
Legacy boot |
|||
EFI boot |
|||
| IP address | IP address of unit | Required | |
| Power user | Username to login | Optional | |
| Power password | Password to access unit | Optional | |
| Power MAC | MAC address of unit | Optional | |
| K_g | K_g BMC key | Optional | |
| Cipher suite | Cipher suite ID | - 17 (17 - HMAC-SHA256::HMAC_SHA256_128::AES-CBC-128) |
Optional |
3 (3 - HMAC-SHA1::HMAC-SHA1-96::AES-CBC-128) |
|||
|
|||
8 (8 - HMAC-MD5::HMAC-MD5-128::AES-CBC-128) |
|||
12 (12 - HMAC-MD5::MD5-128::AES-CBC-128) |
|||
| Privilege level | IPMI privilege level | User |
Optional |
Operator |
|||
Administrator |
Manual power configuration means exactly that – manually configured at the unit – hence there are no parameters to set in the “create machine” UI.
| Form field | Description | Required |
|---|---|---|
| Power address | IP address of unit | Required |
| Power user | Username to login | Optional |
| Power password | Password to access unit | Optional |
| Power hardware address | Hardware address of unit | Required |
HP Moonshot - iLO Chassis Manager
| Form field | Description | Required |
|---|---|---|
| IP for MSCM CLI API | IP address of unit | Required |
| MSCM CLI API user | Username to login | Optional |
| MSCM CLI API password | Password to access unit | Optional |
| Node ID | cXnY | Required |
| - where | X = cartridge number | |
| Y = node number |
Microsoft OCS - Chassis Manager
| Form field | Description | Required |
|---|---|---|
| Power address | IP address of unit | Required |
| Power port | Port where unit is attached | Optional |
| Power user | Username to login | Optional |
| Power password | Password to access unit | Optional |
| Blade ID | Blade ID (usu. 1-24) | Required |
| Form field | Description | Required |
|---|---|---|
| Host UUID | Host UUID | Required |
| Tenant name | Tenant name | Required |
| Username | Username to login | Required |
| Password | Password to access unit | Required |
| Auth URL | URL to access unit | Required |
| Form field | Description | Required |
|---|---|---|
| Power type | Proxmox | Required |
| Host name or IP | Power address for the Proxmox driver | Required |
| Username, including realm | Power user, along with realm (i.e., Username@Realm | Required |
| Password | Required if a token name and secret aren’t given | Provisional |
| API token name | Token name: must include Username without realm (i.e., Username!Token-name | Provisional |
| API token secret | Token secret | Provisional |
| Node ID | VM name or ID | Optional |
| Verify SSL connections… | Boolean, whether or not to verify SSL connections with the system’s root CA certificate | Required |
| Form field | Description | Required |
|---|---|---|
| OpenBMC address | IP address of unit | Required |
| OpenBMC user | Username to login | Required |
| OpenBMC password | Password to access unit | Required |
Christmann RECS-Box Power Driver
| Form field | Description | Required |
|---|---|---|
| Node ID | Node ID | Required |
| Power address | IP address of unit | Required |
| Power port | Port where unit is attached | Optional |
| Power user | Username to login | Optional |
| Power password | Password to access unit | Optional |
| Form field | Description | Required |
|---|---|---|
| Redfish address | IP address of unit | Required |
| Redfish user | Username to login | Required |
| Redfish password | Password to access unit | Required |
| Node ID | Node ID | Optional |
Some of the fields for this power type have fixed choices, indicated in the “Choices” column.
| Form field | Description | Choices | Required |
|---|---|---|---|
| System ID | System ID | Required | |
| Power address | IP address of unit | Required | |
| Power user | Username to login | Optional | |
| Power password | Password to access unit | Optional | |
| Power control type | Password to access unit | IPMI | Required |
| REST API v0.9 | |||
| REST API v2.0 |
| Form field | Description | Required |
|---|---|---|
| Server UUID | Server UUID | Required |
| URL for XML API | XML API URL | Required |
| API user | API user | Optional |
| API password | API password | Optional |
| Form field | Description | Required |
|---|---|---|
| Address | URL of VM | Required |
| Password | API password | Optional |
| Virsh VM ID | libvirt VM UUID | Required |
| Form field | Description | Required |
|---|---|---|
| VM Name | VM name (if UUID unknown) | Optional |
| VM UUID | VM UUID (if known) | Optional |
| VMware IP | IP address of VM | Required |
| VMware username | Username to access VM | Required |
| VMware password | Password to access VM | Required |
| VMware API port | VMware API port number | Optional |
| VMware API protocol | VMware API protocol | Optional |
| Form field | Description | Required |
|---|---|---|
| IP address | IP address of unit | Required |
| Power user | Username to access unit | Optional |
| Power password | Password to access unit | Optional |
How to use the virsh power type
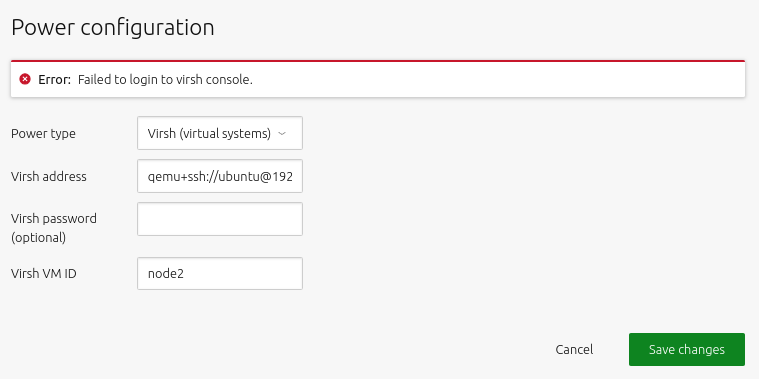
Consider a machine backed by VM. Below, a ‘Power type’ of Virsh has been selected, and the ‘Power address’ of qemu+ssh://ubuntu@192.168.1.2/system has been entered (replace values as appropriate). The value of ‘Power ID’ is the VM domain (guest) name, here node2.
NOTE:
The machine’s hostname – according to MAAS – is a randomly chosen string (here dear.ant). You should change this hostname to something descriptive, that helps you remember why this machine is in your MAAS network.
It’s important to understand that the Webhook power driver is more generic than other drivers, so it has some flexibility that the underlying power driver may not support. For example, Webhook doesn’t require a username or password for the power driver, because not all power drivers work that way. Nevertheless, the power driver you’re connecting to Webhook may actually require a username and/or password. Understanding and implementing these fields correctly for the chosen back-end power driver is the user’s responsibility.
To that end, the “Required” column for this driver refers only to whether Webhook requires a value in each field. Just because a field is optional for Webhook itself does not mean that the underlying power driver will ultimately allow that field to be unspecified.
| Form field | Description | Required (by Webhook) |
|---|---|---|
| Power type | Webhook (from drop-down list) | Required |
| URI to power on the node | URI to access power driver’s API for power on | Required |
| URI to power off the node | URI to access power driver’s API for power off | Required |
| URI to query the nodes power status | URI to access power driver’s API for power status | Required |
| Regex to confirm the node is on | Regex expression that will return a string if the power is on, and no string if the power is off | Required, defaults supplied |
| Regex to confirm the node is off | Regex expression that will return a string if the power is off, and no string if the power is on | Required, defaults supplied |
| Power user | Username to log into the power driver | Optional |
| Power password | Password to access unit | Optional |
| Power token | Power driver API token (used instead of user and password, if set) | Optional |
| Verify SSL connections… | Boolean, whether or not to verify SSL connections with the system’s root CA certificate | Required |
Which BMC drivers are supported
MAAS supports many types of BMC hardware, though not all the drivers have the same capabilities. See the below table for a feature comparison of the BMC drivers currently supported by MAAS.
Tell me about BMC
BMC, or “Baseboard Management Controller,” is an extra micro-controller on the motherboard of a server which forms the interface between system-management software and the device’s hardware. The BMC can collect data from attached sensors, alert administrators to issues, and respond to remote-control commands to control system operation or power state, independent of the system’s CPU.
In the context of MAAS, the BMC is generally controlled by SNMP commands. Any given BMC will function in the context of one or more “power types,” which are physical interfaces that permit use of the IPMI (“Intelligent Platform Management Interface”) protocol. Each power type has a different set of expected parameters required to access and command the BMC.
| Power Driver (X=supported) | PXE Next Boot | Power Querying | Chassis/Pod Configuration | Enhanced UI Error Reporting | BMC Enlistment |
|---|---|---|---|---|---|
| American Power Conversion (APC) - PDU | |||||
| Cisco UCS Manager | X | X | X | ||
| Digital Loggers, Inc. - PDU | |||||
Facebook's Wedge * |
|||||
| HP Moonshot - iLO Chassis Manager | X | X | X | ||
| HP Moonshot - iLO4 (IPMI) | X | X | X | ||
| IBM Hardware Management Console (HMC) | X | X | |||
| IPMI | X | X | X | X | |
| Intel AMT | X | X | X | ||
| Manual | |||||
| Microsoft OCS - Chassis Manager | X | X | X | ||
| OpenStack Nova | X | ||||
| Rack Scale Design | X | X | X | ||
| Redfish | X | X | X | ||
| SeaMicro 15000 | X | X | X | ||
| Sentry Switch CDU - PDU | |||||
| VMWare | X | X | X | ||
| Virsh (virtual systems) | X | X | X |
* The ‘Facebook’s Wedge’ OpenBMC power driver is considered experimental at this time.
How to configure and use IBM Z with MAAS
The IBM Z or LinuxONE system can host MAAS controllers and is able to deploy predefined logical partitions (LPARs) KVM host(s), and virtual machines, if the mainframe is set up properly for MAAS.
The basic architecture is similar to this:
Networking would be structured like this:
Note that net-booting the KVM guests (through the two bridges) can be problematic. There are two options:
-
Adding VNIC characteristics to enable “learning” on the network interface that’s the base for bridge “br2.” This is the recommended approach.
-
Enable full promiscuous bridge port mode at the network interface that’s the base for bridge “br2.” This approach is not recommended because it has some built-in limitations.
MAAS will automatically configure option 1 for you, in case an LPAR is deployed as KVM host (the bridge names may differ).
In order to achieve this configuration, there are a number of steps that must be executed; specifically, you must know how to:
- Evaluate IBM Z requirements
- Login to the IBM Z
- Set up a suitable partition for MAAS
- Set up networking for MAAS
- Set up storage for MAAS
- Set the partition boot parameters
- Set up your IBM Z virtual machines for enlistment
The MAAS controller does not necessarily need to run on an LPAR on the IBM Z system itself, but can also run on a different system outside. But since the MAAS controller requires a network connection to the hardware management console (HMC), it is recommended to keep it co-located and (for security reasons) as close as possible to the HMC and run it in a dedicated LPAR.
Such a MAAS controller LPAR should have at least two SMT hardware threads (one IFL), since it runs several services (bind, rack-, region-controller and more), 16 GB RAM and 100 GB disk space - recommended is to use the double amount of these resources.
The resources of the LPARs to deploy on (‘machines’ in terms of MAAS) depending on the use case. LPARs that are deployed as KVM host would of course require significantly more resources to be able to host KVM guest on top.
There are several constraints on the definition and setup of the ‘machine’ LPARs - please see below.
The system requirements to host MAAS and its virtual machines on the IBM Z platform are as follows:
- IBM z14 GA2 (or newer) or IBM LinuxONE III (or newer)
- HMC running in DPM mode (mandatory, traditional mode is not supported!)
- HMC firmware level H39 - (HMC at H40 and SE at S55)
- HMCs Rest-API enabled
- python-zhmcclient (0.29 or later) running on the MAAS controller system, connected to the HMC
- HMC user ID for the zhmcclient access to the HMC API (must have permissions for the “Manage Web Services API Logs” role and “Manage Web Services API Logs” role)
- I/O auto-configuration enabled for the ‘machine’ LPARs
- zFCP (SCSI) disk storage (only, no DASD support), recommended are two disks, one defined as type ‘boot,’ the second as type ‘data’
- a dedicated storage group per ‘machine’ LPAR; these must include the dedicated zFCP storage for this particular managed LPAR only (‘boot’ and ‘data’ for LPAR n) - but no additional shared storage!
- qeth network devices (Hipersockets or OSA, recommended); at least one qeth NIC, recommended two (or more)
- Ubuntu Server 20.04 installed on a dedicated system (LPAR or PC), that acts as MAAS Controller
- one or more LPARs as ‘machines’ (aka MAAS deployment targets)
Be aware that these are minimum system requirements.
Access the HMC and login to the IBM Z
To login to the HMC, you must have at least “system programmer” privileges. Gaining that level of access is beyond the scope of this document. Once you are sure that you have the necessary access, you first need to navigate to the Hardware Management Console (HMC) application in your Web browser:
Click on the “Log on…” link, which will bring you to a login screen:
Upon successfully logging on, you will land on the Welcome Screen:
Select the “Tasks Index” on the left-hand navigation:
From here, you will be able to access the commands needed to prepare your IBM Z to host MAAS.
Set up a suitable IBM Z partition for a MAAS machine
In order to prevent MAAS from taking over the entire system, you must assign both the controller and the ‘machines’ / KVM hosts to specific partitions, with suitable limitations. To set up suitable IBM Z partitions for hosting MAAS, you must choose “Partition Details” from the “Tasks Index,” which will bring you to a screen like this one:
You must then choose the “target object” (in this case we’ve chosen TA05) to be operated upon:
Click “OK,” and you’ll arrive at a screen similar to the one below:
Make sure you’re on the “Partitions” tab, and select the desired object (“TA05…”):
Right-click on the selected object and select “Partition Details:”
On the “General” tab, edit the partition details to suit your proposed MAAS deployment:
Next, you will set up the networking details for this partition, as shown in the following section.
Set up IBM Z networking for a MAAS machine
To properly enable networking within the IBMZ partitions, you must change to the “Network” tab under “Partition Details:”
Click on the NIC of interest to bring up the “NIC Details” screen:
Confirm that the parameters on this screen are consistent with your planned MAAS deployment, then bring up the network adapter(either OSA or Hipersockets) by selecting it:
Ensure that all settings on the “General” tab conform to your planned MAAS deployment; then select the “Network Interface Cards” tab on the left-hand navigation:
Again, ensure that the parameters associated with the networking arrangement are consistent with your planned MAAS deployment.
Next, you will set up the storage layout for your MAAS partition(s).
Set up IBM Z storage for a MAAS machine
To set up suitable storage for a MAAS deployment, you should bring up the “Partition Details” for your chosen MAAS partition and select the “Storage” tab from the left-hand navigation:
Choose the “VOLUMES” sub-tab, and lick on the hyperlinked partition name to bring up the storage configuration tab:
Click on “GET DETAILS” for the Boot Volume in the Volume list to bring up the “Configuration details” screen:
Ensure that the Boot Volume is configured appropriately for your planned MAAS deployment, then click “Done.” Then return to the storage configuration tab and choose the Data Volume, and tune it to the appropriate parameters.
Next, choose the “ADAPTERS” sub-tab to bring up information on the storage adapters:
Set any necessary parameters to conform to your planned MAAS deployment.
Set the partition boot parameters
Return to the “Partition Details” screen and select the “Boot” tab in the left-hand navigation:
Change any settings as necessary to support your planned MAAS deployment.
Set up your IBM Z virtual machine for enlistment
To cause IBM Z KVM partition guests to enlist, it’s necessary to manually put in the BMC information for each guest. MAAS can then detect the guest, enlist it, and boot it as necessary.